This post comes in addition to my previous post: RPi-Monitor: Security and authentication with a reverse proxy.
You may notice that your browser do not trust the certificate we generate consider it as insecure. In this post we will see how to create our own certificate and certificate authority. We will also see own to configure our browser to trust our certificate authority and consider the associated certificates as secure.
Thanks to this actions, we will then move fromhttps :-( to https :-) and remove the security warning.
Note: Certificate generation has been extracted from a very interesting doc found in http://zepala.free.fr/?q=book/export/html/49.
Create a multi-sites certificate
To create the certificates we will need to execute numerous commands. These commands have been gathered into scripts that can be download from RPi-Monitor repository on Github
Downloads make_ca.sh, make_cert.sh, openssl.cnf from Github directly on you RPi:
wget http://goo.gl/amRwq -O make_ca.sh
chmod +x make_ca.sh
wget http://goo.gl/ERmln -O make_cert.sh
chmod +x make_cert.sh
wget http://goo.gl/PCSkE -O openssl.cnf
Customize openssl.cnf and update the fields related to identity and network.
Execute make_ca.sh and answer to the questions to create the CA ROOT
Execute the following command and choose server then answer to the questions to create the certificate.
make_cert.sh RPi-Experiences
Install the certificate on server
Copy certificates for nginx and shellinabox:
sudo cp sslcert/private/RPi-Experiences-key.pem \
sslcert/public/RPi-Experiences-cert.pem \
/etc/ssl/localcerts/
sudo sh -c "cat sslcert/private/RPi-Experiences-key.pem \
sslcert/public/RPi-Experiences-cert.pem > \
/var/lib/shellinabox/certificate.pem"
Copy the cacert.pem and certificate.p12 into RPi-Monitor web root:
sudo cp sslcert/public/cacert.pem \
/usr/share/rpimonitor/web/
sudo cp sslcert/public/RPi-Experiences-bundle.p12 \
/usr/share/rpimonitor/web/certificate.p12
Restart nginx and shellinabox
sudo service nginx restart
sudo service shellinabox restart
Install CA ROOT and certificate with Google Chrome under Linux*
You may notice that your browser do not trust the certificate we generate consider it as insecure. In this post we will see how to create our own certificate and certificate authority. We will also see own to configure our browser to trust our certificate authority and consider the associated certificates as secure.
Thanks to this actions, we will then move from
Note: Certificate generation has been extracted from a very interesting doc found in http://zepala.free.fr/?q=book/export/html/49.
Create a multi-sites certificate
To create the certificates we will need to execute numerous commands. These commands have been gathered into scripts that can be download from RPi-Monitor repository on Github
Downloads make_ca.sh, make_cert.sh, openssl.cnf from Github directly on you RPi:
wget http://goo.gl/amRwq -O make_ca.sh
chmod +x make_ca.sh
wget http://goo.gl/ERmln -O make_cert.sh
chmod +x make_cert.sh
wget http://goo.gl/PCSkE -O openssl.cnf
Customize openssl.cnf and update the fields related to identity and network.
Execute make_ca.sh and answer to the questions to create the CA ROOT
Execute the following command and choose server then answer to the questions to create the certificate.
make_cert.sh RPi-Experiences
Install the certificate on server
Copy certificates for nginx and shellinabox:
sudo cp sslcert/private/RPi-Experiences-key.pem \
sslcert/public/RPi-Experiences-cert.pem \
/etc/ssl/localcerts/
sudo sh -c "cat sslcert/private/RPi-Experiences-key.pem \
sslcert/public/RPi-Experiences-cert.pem > \
/var/lib/shellinabox/certificate.pem"
Copy the cacert.pem and certificate.p12 into RPi-Monitor web root:
sudo cp sslcert/public/cacert.pem \
/usr/share/rpimonitor/web/
sudo cp sslcert/public/RPi-Experiences-bundle.p12 \
/usr/share/rpimonitor/web/certificate.p12
Restart nginx and shellinabox
sudo service nginx restart
sudo service shellinabox restart
Install CA ROOT and certificate with Google Chrome under Linux*
* Note: I tried to install certificate on Windows but I didn't success. As I don't use Windows as my day to day OS, I stopped my investigation. I'm sorry for the 80% of people not using Linux... It is maybe time to jump into the open world! :-). If you succeed to install this certificate on Windows or other operating system your comments are welcome. A good starting point for such a thing would be to read CA Cert documentation.
The first step will consist to download certificate and CA ROOT. This can be done from your server at the following addresses:
https://RPiIpAddress/rpimonitor/cacert.pem
https://RPiIpAddress/rpimonitor/certificate.p12
Now, open Google Chrome and select settings:
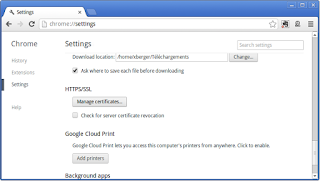
At the bottom of the settings page, click on Show advanced settings...:
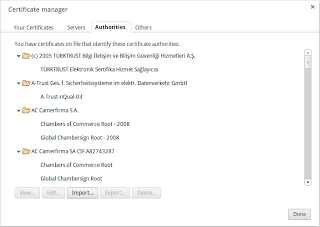
Select the tab Authorities and click on Import...:
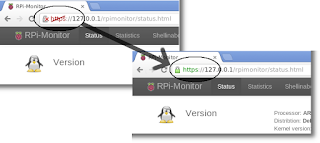
Now the certificate the the CA ROOT are imported. Restart Google Chrome and connect to RPi-Monitor. You should have the security warning and the https lock icon should be green.
The first step will consist to download certificate and CA ROOT. This can be done from your server at the following addresses:
https://RPiIpAddress/rpimonitor/cacert.pem
https://RPiIpAddress/rpimonitor/certificate.p12
The content of cacert.pem will be displayed in screen, save is as a file named cacert.pem
At the bottom of the settings page, click on Show advanced settings...:
Click on the button Manage certificates...:
Select the tab Authorities and click on Import...:
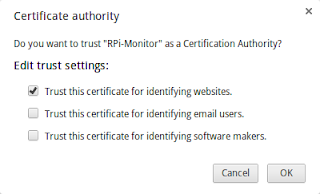
Select the file cacert.pem previously downloaded and import it. The following message box will appear.
Check Trust this certificate for identify website and click OK.
The Certificate Authority is now installed. We will now install the certificate which will authenticate our web site. Select the tab Trust Certificates and click on Import....
Import the file certificate.pk12 previously downloaded.
| Image may be NSFW. Clik here to view. 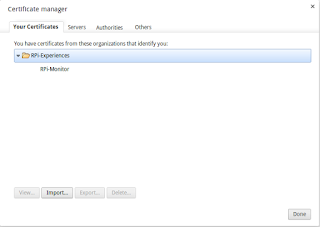 |
| Note: In this screenshot, the certificate has already been imported |